
THOUSANDS OF SUCCESS WORDPRESS SITE hijacked
The WordPress Site hackers seem to continue being able to find new loopholes in various platforms to attack malware to users who are unfamiliar. Most recently, the successful hacker hijack thousands of websites that operate using a CMS (content management system) made WordPress and use it to spread viruses on the relevant website visitors.
This attack was recorded beginning to be waged around the beginning of September, but the number of websites that have now been successfully hijacked directly menigkat sharply within the last 48 hours. If on Tuesday the number of attacks launched generally range between 1000 websites per day, Thursday the number increased to 6,000 websites per day.
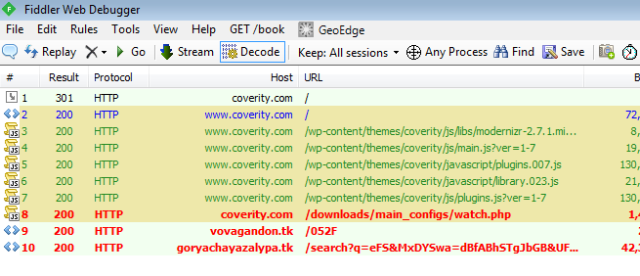
This discovery was expressed by Daniel Cid of internet security firm Sucuri; in a posting on the blog, Cid explained that the website has been hijacked used to redirect visitors to a server that serves as the host of a malware code are available through a special device for the purposes of piracy called Nuclear. These devices are often found on the black market, where the server is eventually going to use a wide variety of attacks on any access, depending on the type of OS and applications used to access.
Sucuri noted that of the thousands of successful website hijacked, 95% of them using WordPress engine. Sucuri still not provided a description of how websites can be hacked, but they suspect that the source of the problem lies in that there is a gap in the WordPress plugin. Google also act quickly to immediately blacklisted 17% of the sites suspected to have been hijacked, also memberikat extra warning when users would access the relevant website.
If you happen to also use the CMS of WordPress to your personal website, just perform scanning through Sucuri to ensure that your website is safe from attack.








Leave a Reply